This blog post is going to be about the adventure I had doing some OSINT
on MuddyWater APT. It starts off when on Telegram a bunch of new leaks
were coming out involving APT34 tools be leaked online, Data, and member
data also. I started to do some research around to who maybe might be
involved, when I came across MuddyWater Macro Document. While doing some
analysis on the document I came across something interesting..
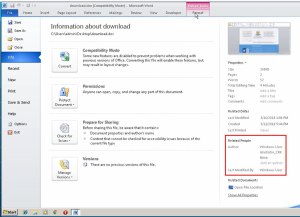
We see here that the Author of this document is a Windows User
“Gladiator_CRK” “Nima” So I went ahead and started googling around
“Gladiator_CRK” and came up with some interesting things. This Youtube
video here from 2018 https://www.youtube.com/watch?v=wkWiFzipbpw
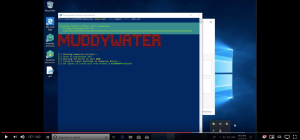
This shows a PoC bypassing Kaspersky Anti-Virus with ascii of MUDDYWATER. Which is pretty interesting since the Youtube account is also named muddy water and when we scroll down we see a comment with someone named “Nima Nikjoo”.
Now this get’s interesting so I go ahead and take that name and throw it in Google which gives us some nice output.
I go ahead and view the first link which is a Twitter account made by Nima, Which ended up when I logged in was following me on Twitter lol…
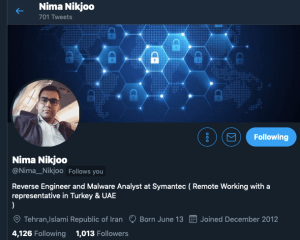
We engaged in a talk about some things and Nima then gave me his Telegram to talk further. I found something interesting after our talk was done and once I added him he had a Russian/Serbian username which I thought was weird and decided to translate it.

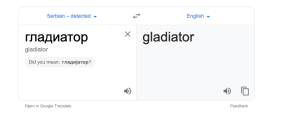
Well.. Now I’m really starting to thing we have a good guess that Gladiator_CRK is Nima Nikjoo. So let’s take a look at some more information I was able to gather, We have some python code that generates a macro embedded in PowerShell from MuddyWater.
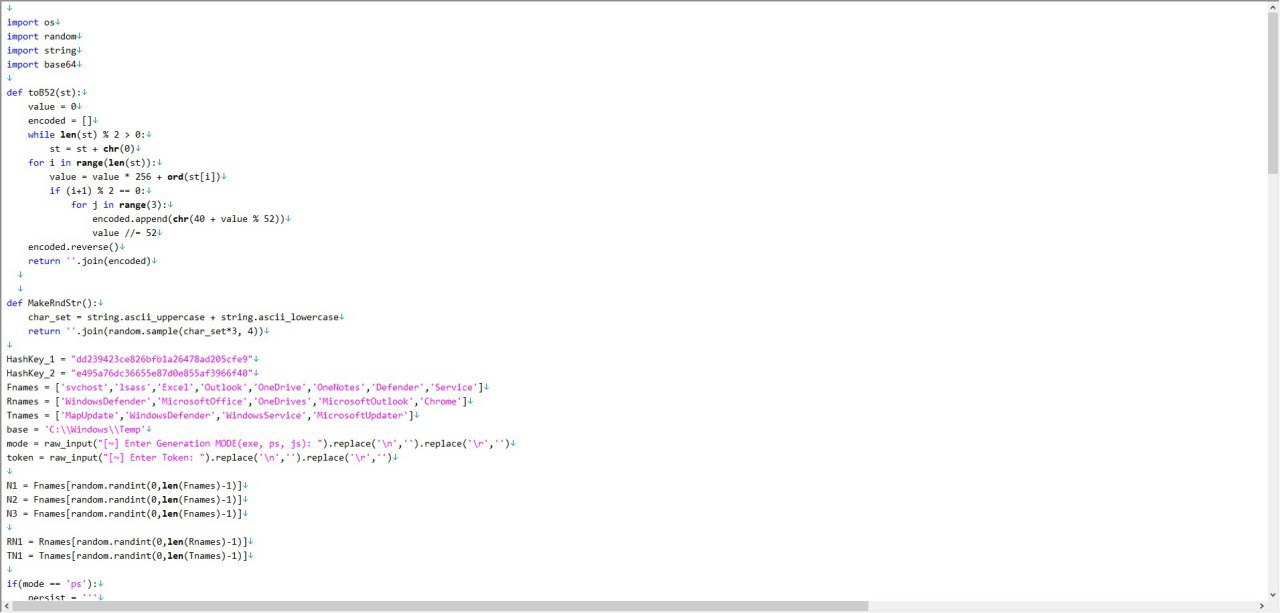
There are two hashes labled as “HashKey_1″and “HashKey_2” If we decrypt these hashes this is what we get. dd239423ce826bfb1a26478ad205cfe9 gladiator_crd e495a76dc36655e87d0e855af3966f40 nima.n
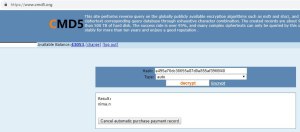
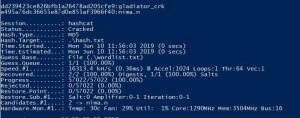
Interesting the output for both of those hashes are the same names we
have come across so far. Let’s take a look at another example.
Here we have the PoC code(Not Public) I was able to obtain through other
means and this shows “#GMER EDITION from N.N.T” which I thought was
interesting for initials, So I wanted to find out what this means.
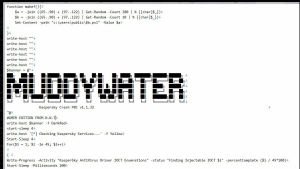
I found out that Nima has his own website @ https://www.vsec.ir and of
course we go and do some information gathering on this and we come up
with domain: vsec.ir
ascii: vsec.ir
remarks: (Domain Holder) Nima NikjooyeTabrizi
remarks: (Domain Holder Address) No.988, Shahid Khorasani Sq East Azerbaijan, IR
Nima Nikjoo Tabrizi => N.N.T
While looking though more information online I came across a blog post
about Iranians Behind StoneDrill and NewsBeef Malware
@ https://irancybernews.org/news/318/ if we scroll down through the
article we find something else, We see that Nima looks like he has some
history as well before MuddyWater.

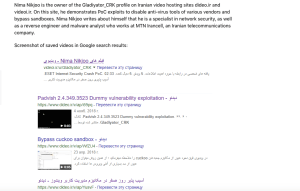
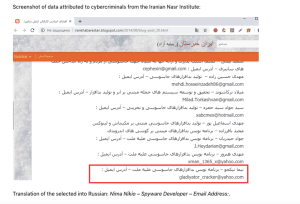
I also found out today another blog that looks like it’s been Google
cached but shows a good insight into some more information with Nima
included.
“Muddy waters: how MuddyWater hackers attacked a Turkish military electronics manufacturer”
https://webcache.googleusercontent.com/search?q=cache:8hHKsokcpJkJ:https://prog.world/muddy-waters-how-muddywater-hackers-attacked-a-turkish-military-electronics-manufacturer/+&cd=15&hl=en&ct=clnk&gl=uk&client=firefox-b-d

So this is a quick insight of what I’ve been up too mix with work related things. If anyone else has anything else interesting about MuddyWater or Actors behind it let me know! I will be updating this blog post with more information later once I get more organized with the rest. Just a quick write up.








